VMware vSAN is Software-Defined Storage(SDS) solution from VMware that is fully integrated into vSphere. To enable vSAN, we need to have a minimum of three ESXi hosts, and each host needs at least one cache disk and one capacity disk. The local disks of ESXi hosts should be formatted by VMFS. Since vSAN is a vSphere clustering feature, we should also have Center Server in place before start implementing it.
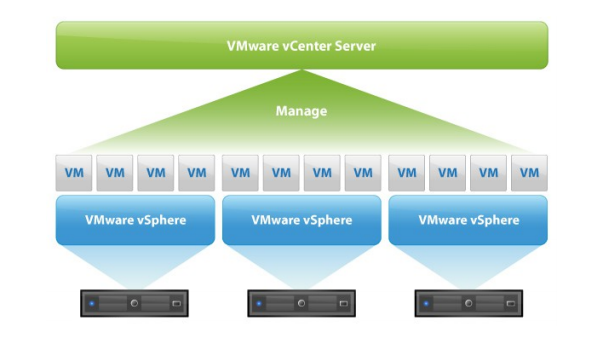
If you are a System Administrator or even a Solutions Architect, you might a face a challenge to build a vSAN Cluster with minimum ESXi servers without having a vCenter in place. In many green field environments, vCenter has not been installed and you want to keep ESXi’s disks intact and unformatted. In addition, there are some customers that want to build and manage vSAN Cluster in a separate vCenter and they do not have any additional ESXi host for vCenter deployment.
Continue reading “vSAN Deployment without existing vCenter Server”