In September 2022, an announcement was made about the release of vSphere 8 with new features and capabilities. Building on this momentum, the subsequent release of vSphere 8U1 brings new enhancements and improvements into three different categories of operating efficiency, elevated security, and supercharged workloads. So, by these pillars, customers can operate their infrastructure more efficiently, securely, and agile. So let’s start with the new enhancements in vSphere 8U1.
Operating efficiency
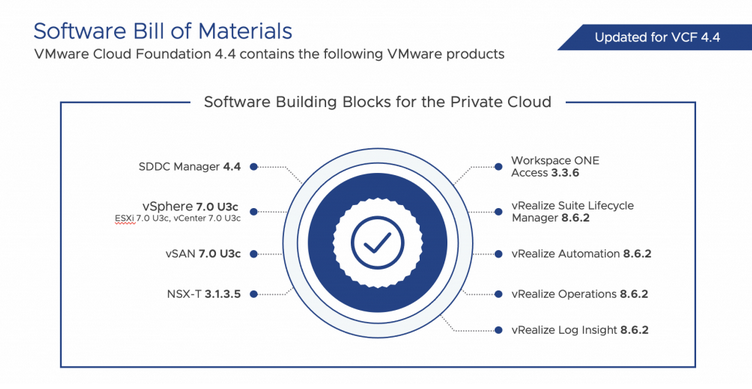
In vSphere 8, vSphere Configuration Profiles were introduced as a tech preview with some limitations of not supporting vSphere Distributed Switch and NSX. If you have not checked this functionality, read my blog post on what’s new in vSphere 8, which explains this functionality in more detail. But In vSphere 8U1, vSphere Configuration Profile is now fully supported and allows administrators to apply the homogenous configuration at the cluster level.
So you can set the desired configuration at the cluster level in JSON format and check the compliance of the hosts in the cluster; if they are not compliant, you can remediate the hosts to become compliant. But one point to remember, If the cluster has a Host profile attached to it, you will get a warning to remove the Host profile when you want to move to vSphere Configuration Profile. When you transition, you can no longer attach host profiles to the hosts within the cluster. vSphere Configuration Profiles now supports vDS configuration, and it can be activated when you create a new cluster, but environments with NSX still can’t use this technology.
Continue reading “What’s New vSphere 8 Update 1”