When it come to setting up a hybrid cloud environments, one of the most important topics is networking. It is usually comes down to stretch on-prem network segments to the public cloud environment. This blog post is going to simply describe NSX-T architecture on AVS as the default networking and security stack. If you are new to AVS you can read Introduction to AVS blog post first, and then continue with this article.
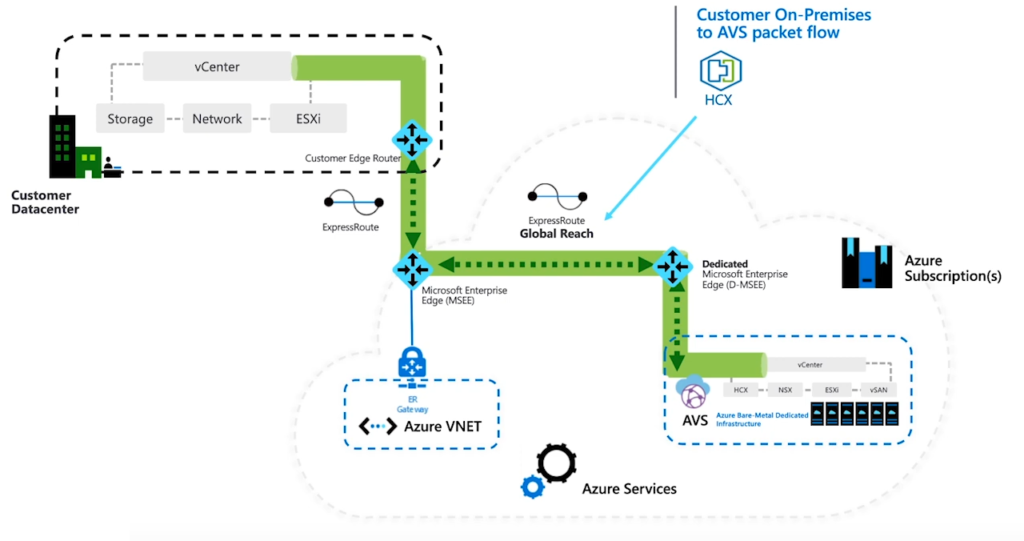
When you deploy AVS, VMware NSX-T will be install and fully configured as the default networking stack. In fact, NSX Manager/Controllers will be installed, all ESXi hosts(AVS nodes) will be prepared as Transport Nodes and Edge Transport Nodes will also be deployed. All the pre-provisioned NSX-T objects are going to be protected through use of principal identity. So you don’t need to worry about the initial deployment and configuration and even integrity of default configuration of NSX-T on AVS SDDC. So NSX-T will be deployed on AVS during the initial implementation and even more, below logical components will be configured to provide north-south and east-west connectivity.
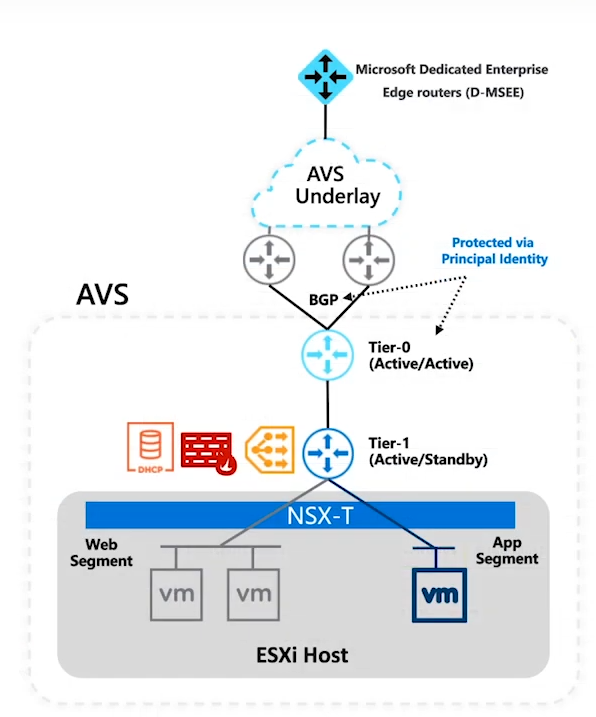
If we dig a bit deeper on logical configuration of NSX-T on AVS, a Tier-0 gateway in an Active/Active HA mode with ECMP configuration. This Tier-0 gateway will act as northbound gateway and a default BGP peering will be configured towards Azure underlay. Below this Tier-0 gateway, a Tier-1 gateway will be provisioned as a tenant-based router. We can use this Tier-1 gateway if we want to implement additional services like load balancer, gateway firewall and even DHCP services. Underneath this Tier-1 gateway, we can create segments, connect our workloads and this Tier-1 gateway will be take care of east-west routing. There is also possibilities to deploy additional Tier-1 gateways, enable Distributed Firewall(DFW) and other advanced services.
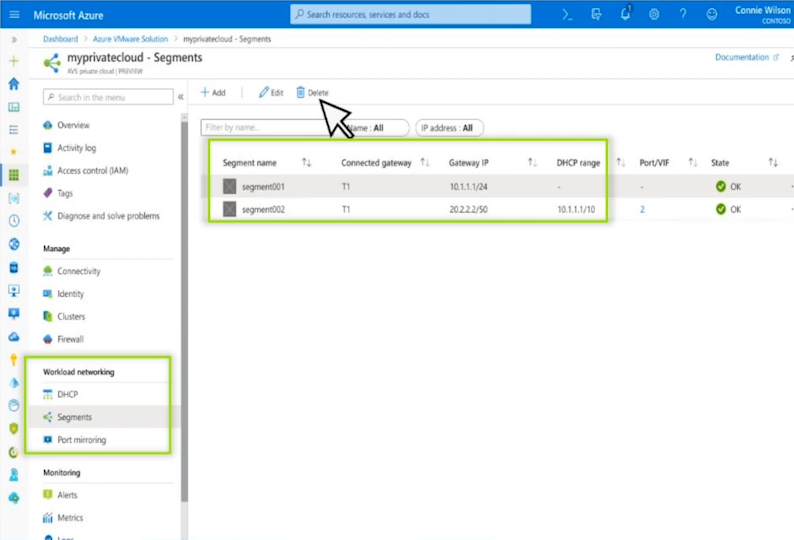
So if you are not a NSX-T expert, don’t worry because all NSX-T infrastructure will be per-provisioned in background. You even get access to a simplified NSX-T interface which you can create segments and enable networking services.
To discuss AVS Hybrid Networking further, we will go through the IPSec VPN set up between on-prem and AVS in the next blog post.